Unpacking Emotet malware part 01
As-salamu Alaykum
Introduction
Emotet is a Trojan that spreads through spam emails. The infection may arrive either via malicious script, macro-enabled document files, or malicious link. 1
Download the sample: Here
MD5: CA06ACD3E1CAB1691A7670A5F23BAEF4
Virustotal VT
we can see that the malware is detected by 57 out of 68 as a trojan.
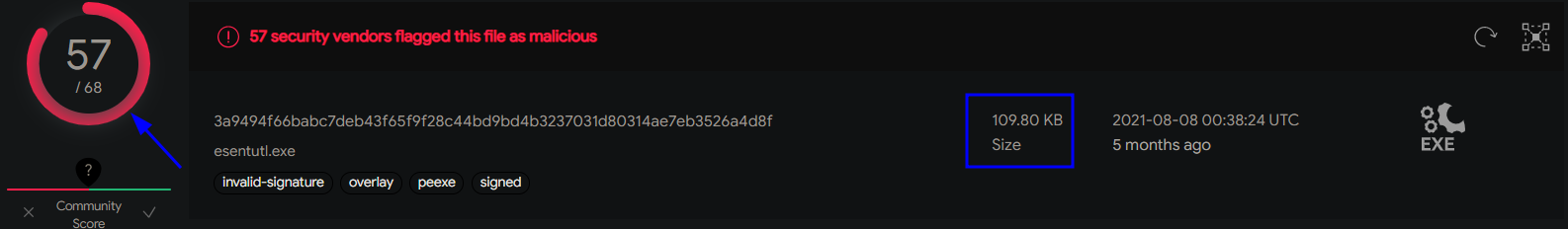
Size: 109.80 KB (112440 bytes)
In Details section VT Details
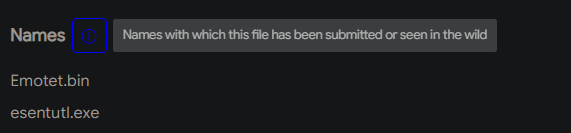
1- Different names of the sample
2- Header info
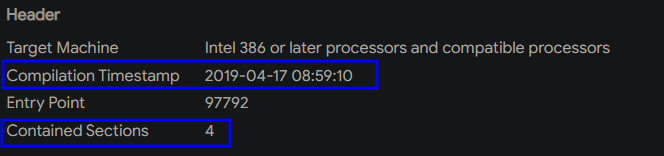
Shows compilation Timestamp which can be changed. and Shows number of sections
DiE
open DiE to get more info about the sample
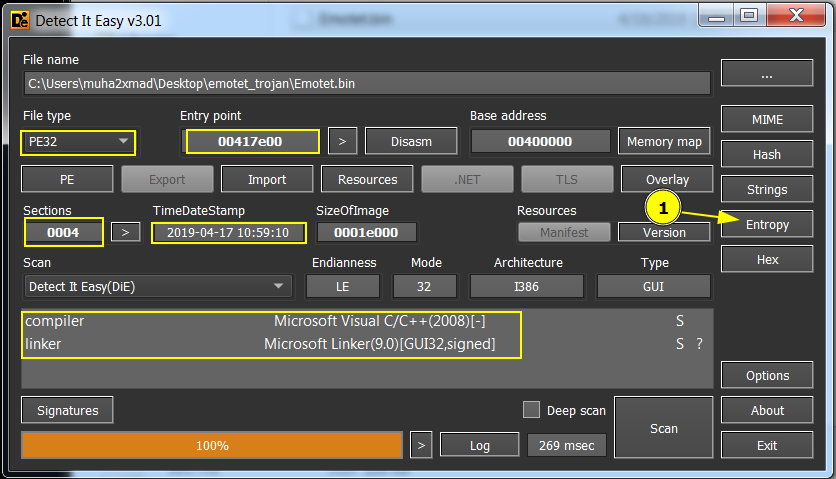
As we see that info about file type, Entry point, and sections. It will help us in our analysis
Entropy:
press over “Entropy” as in the previous figure(4)
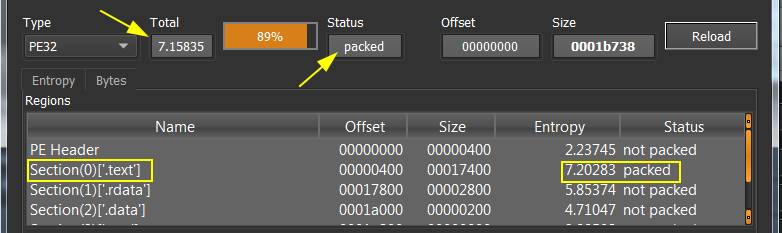
Shows that it has high entropy in .text section which is an indicator to be packed
PEstudio analysis
Indicators section:
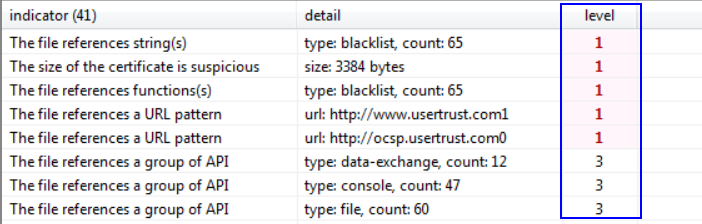
*Level 1 is most malicious and bigger numbers “3” are less malicious. Shows different malicious indicators that help us in the analysis.
Sections section:
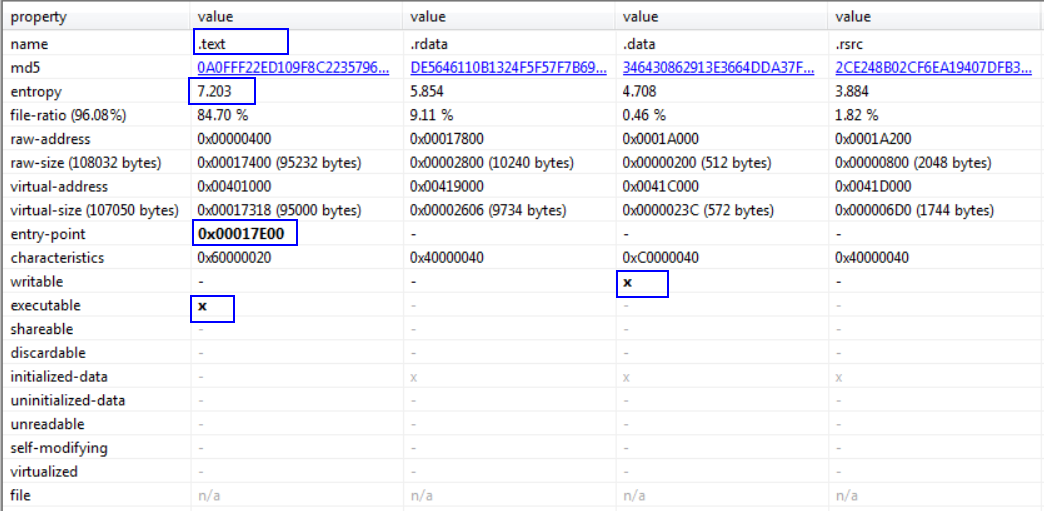
The previous figure shows:
1- .text section is packed
2- .text section contains the entry point for the executable. This means that, in addition to holding the compressed data, .text section also contains the stub code responsible for unpacking. 2
*The section which is responsible for unpacking can vary as in UPX packing
3- .text section is executable
4- .data section is writable
Strings section:
press over blacklist to list them
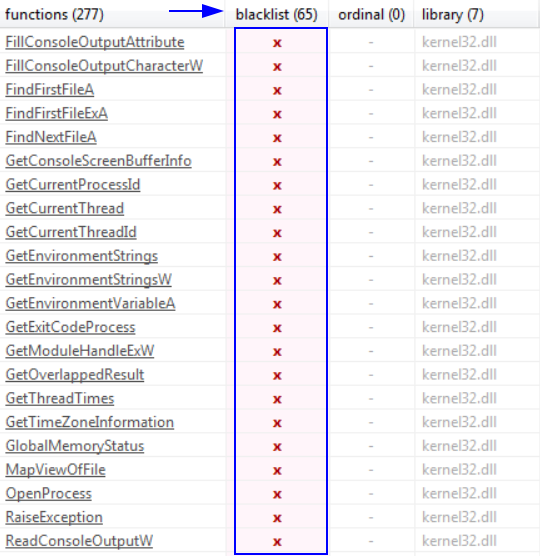
Strings are good indicators to know what this malware is trying to do on the system
IDA analysis
To analyze the assemble code to know how to unpack and where to start the debugging
Open it in IDA: It shows that is low number of functions which another indicator that is packed
Press over “start” which located in the function as in the previous figure to get started
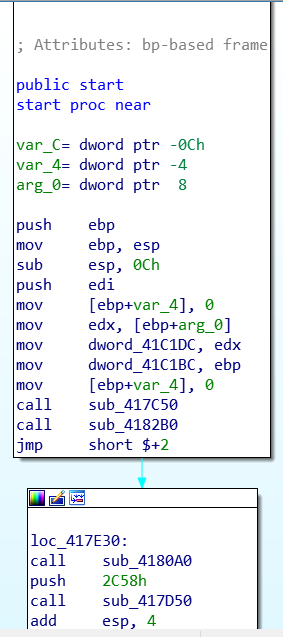
Because Emotet malware uses a customized packer. we can try to unpack it through dynamic analysis. Through dynamic analysis the malware does the unpacking process. The process will need to allocate memory for the next stage.
So it’s a good assumption that we will see a call to VirtualAlloc. We need to search which function has VirtualAlloc call. 3
If you searched you will find that call sub_417D50 is the unpacking routine
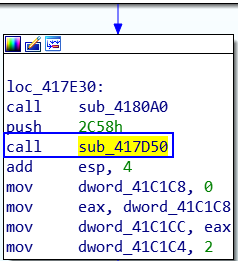
This our unpacking function: sub_417D50
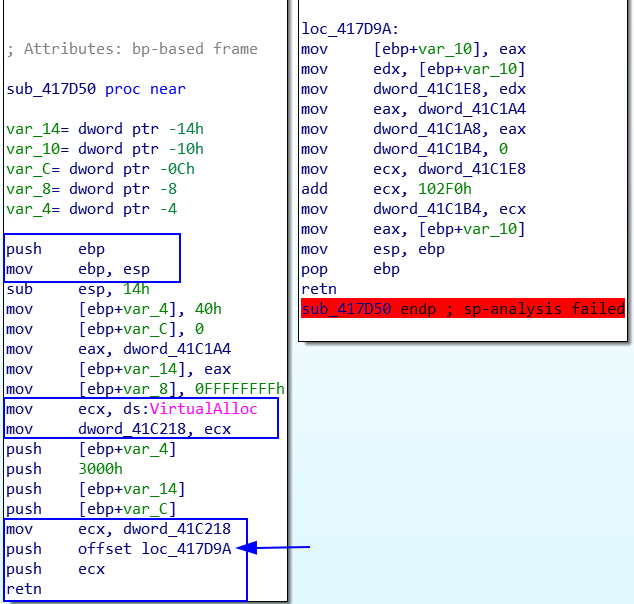
Abnormal prologue
First we need to clear what normal epilogue and prologue are? The procedure prologue and epilogue are standard initialization sequences that compilers generate for almost all of their functions.

What is NOT normal here is epilogue in the last figure:
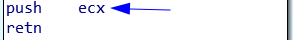
you don’t push anything before ret this called abnormal.
normal epilogue is to pop EBP before ret. Here it will return ecx because it executes the last instruction- top of the stack.
And the real return is from this function loc_417D9A because this is 2nd top of the stack.
We need to know what is happening in this function?
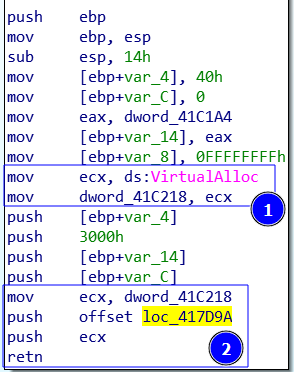
In the last figure we see the coming:
VirtualAlloc is moved to ECX, then
ECX is moved to dword_41C218, then
dword_41C218 is moved to ECX
then push ECX and then ret
And the real return is from this function loc_417D9A
So we need to know the address of this function to set a Breakpoint in x64dbg by pressing space.
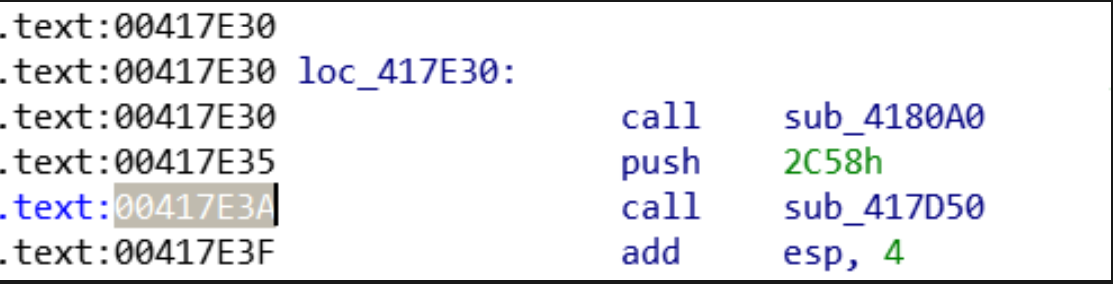
We know that code is packed. We search for abnormal jumps:
jump or call Instructions to registers
Jump to strange memory addresses (long jump)
Why searching for abnormal jumps? the address to the location of where data is being unpacked to is stored in a register (such as ecx), and that memory address is often in an entirely different section.
I will write an article about “indicators of packed file”. InshAllah
If we return to start function and search you will find it.
Here we see our abnormal jmp ecx:
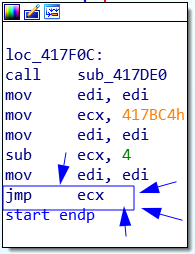
Press space to get its address: 00417F1F.

How to Unpack in the next part. InshAllah
edit: part 02
article quote
المنازل العليا لا تُنال إلّا بالبلاء
References
Inspired by: https://malgamy.github.io/malware-analysis/Emotet-Malware-0x01/
2- https://malware.news/t/the-basics-of-packed-malware-manually-unpacking-upx-executables/35961
3- https://distributedcompute.com/2020/02/20/unpacking-emotet/
