Unpacking Emotet malware part 02
As-salamu Alaykum
Part 01 summary
Download the sample: Here
found VirtualAlloc call in sub_417D50 and its address.
we search for abnormal jumps. we found jmp ecx and its address.
Introduction
we will debug our sample with x32dbg tool to unpack the Emotet malware
Notes to be taken
-
What is Packing: A trick which is Used to avoid AV detection and analysis.
-
What is a packer: A tool that compresses, encrypts, and/or modifies a malicious file format. 1
-
Why using packers: To avoid AV detection and analysis to make it harder for researchers to analyze the code
-
We need to find the the original entry point (OEP). What is the OEP: is the address of the malware’s first instruction (where malicious code begins) before it was packed. 2
-
How to find the OEP: find the
tail jump. the tail jump It’s an unconditional jump exists in the tail of stub code , it points to address of unpack file. 3
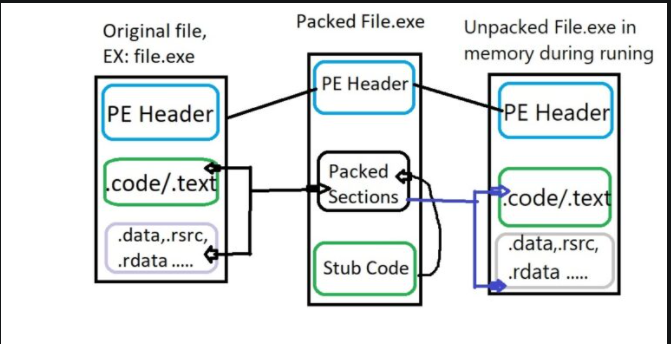
How to the unpack happen? 3 As we see in the figure (1). OS create stub code with packed file
- What is stub code? 3 Stub code is responsible for unpacking packed sections, when you are running the file ,the address of unpack file exists in the stub code to unpack file. So at the end of the stub code we will see an unconditional jump (tail jump), that is meant after execute the stub code will jump to the address of unpacking file.
What is stack string? answer
We need to know what is VirtualAlloc? Here
Says that “Reserves, commits, or changes the state of a region of pages in the virtual address space of the calling process. Memory allocated by this function is automatically initialized to zero.”
Syntax
LPVOID VirtualAlloc(
[in, optional] LPVOID lpAddress,
[in] SIZE_T dwSize,
[in] DWORD flAllocationType,
[in] DWORD flProtect
);
The most important parameter of this function is lpaddress, which returns the starting offset of the newly allocated memory. where we will extract the malware then dump it.
Start Debugging
Open our sample by x32dbg and hit the entry point
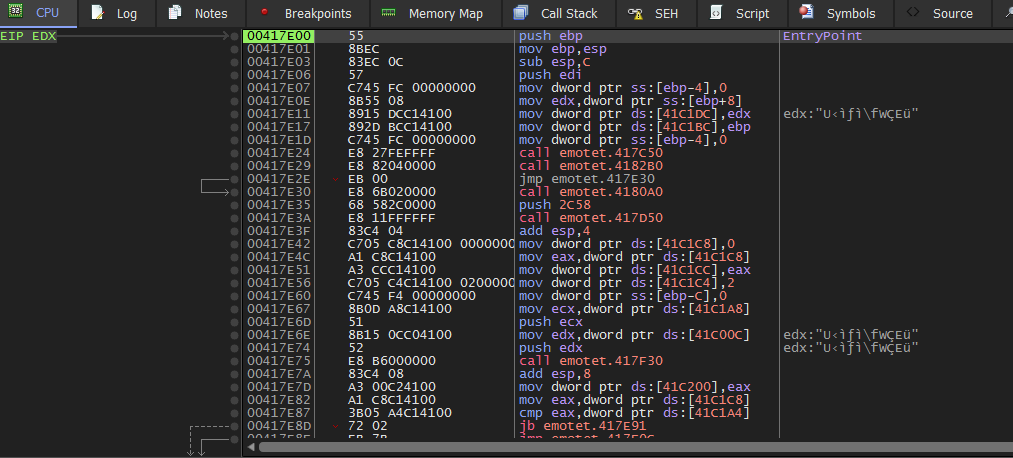
We set a breakpoint over the jump instruction jmp ecx at the address 00417F1F by pressing f2.
because after this jump the unpack process will happen.
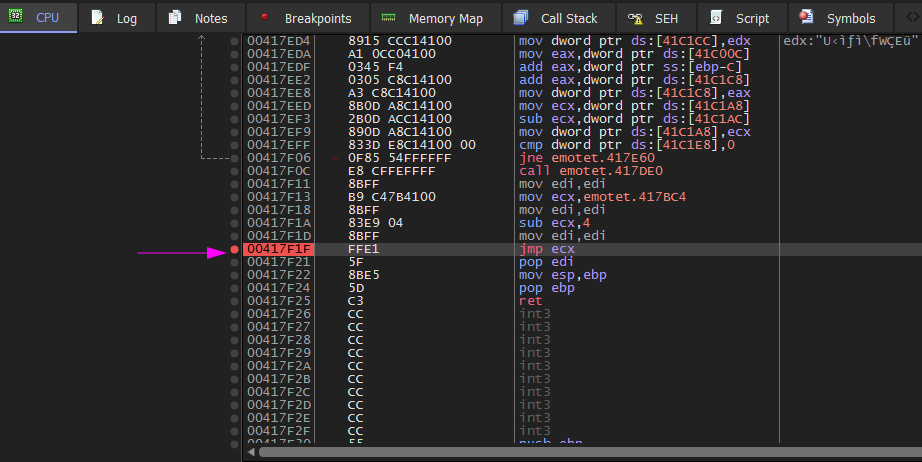
Then we press f9 to hit the breakpoint.
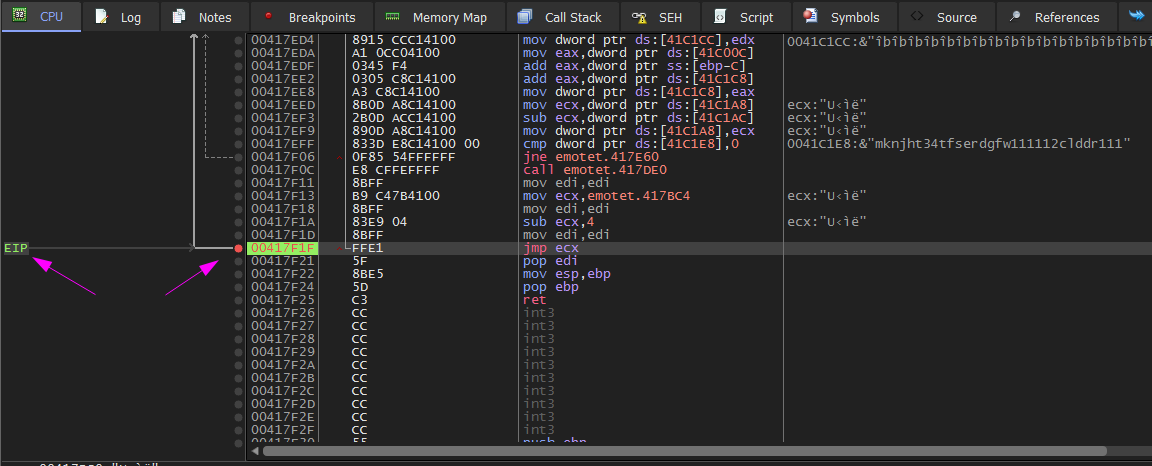
Then press f7 we jump to another function. If we analyze this function we will notice that:
epilogue
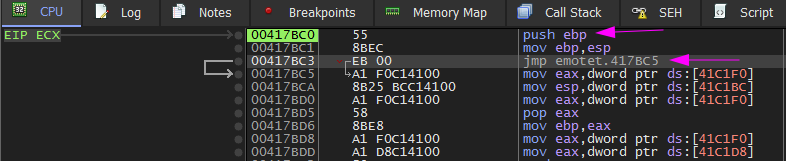
Abnormal prologue
The last figure shows the abnormal prologue (1). And (2) is a suspecious instruction which we will know late that is new VirtualAlloc.
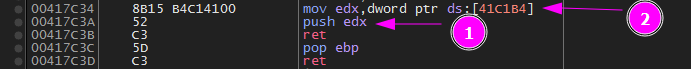
So we set a breakpoint over this instruction mov edx,dword ptr ds:[41C1B4] by f2 and press f9 to hit the breakpoint.
Now if we follow in dump We see that it’s allocating memory.
Then Press f8 it will push edx to the stack which is the value of mov edx,dword ptr ds:[41C1B4].
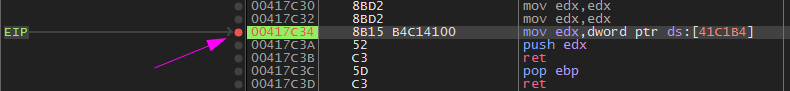
Then Press f8. There is abnormal ret. Normal ret value will get back to wherever it was called from.
Here it return to this address 002302F0. Which will be the address of the unpacking section.
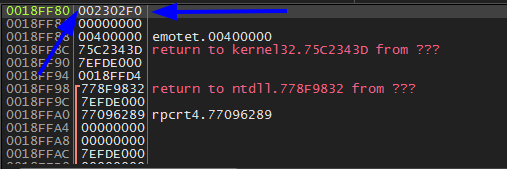
So step over it.
In the next part we will see functions (Unpacking routine) and we will explain it on the fly in the next figure
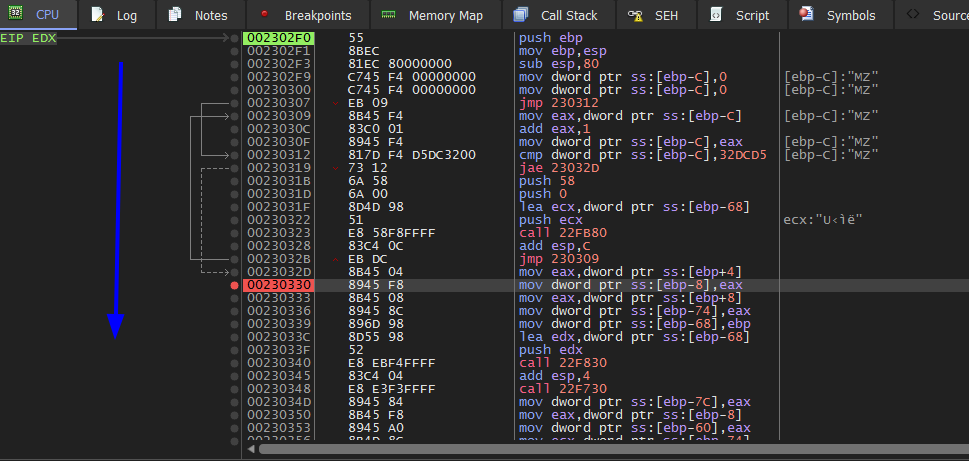
Keep stepping over untill you reach the breakpoint.
Then we see this funtion and step into f7.
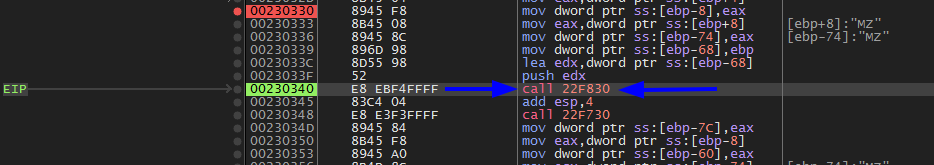
It uses stack strings. which is mentioned above In introduction. (1) pushes them on the stack.
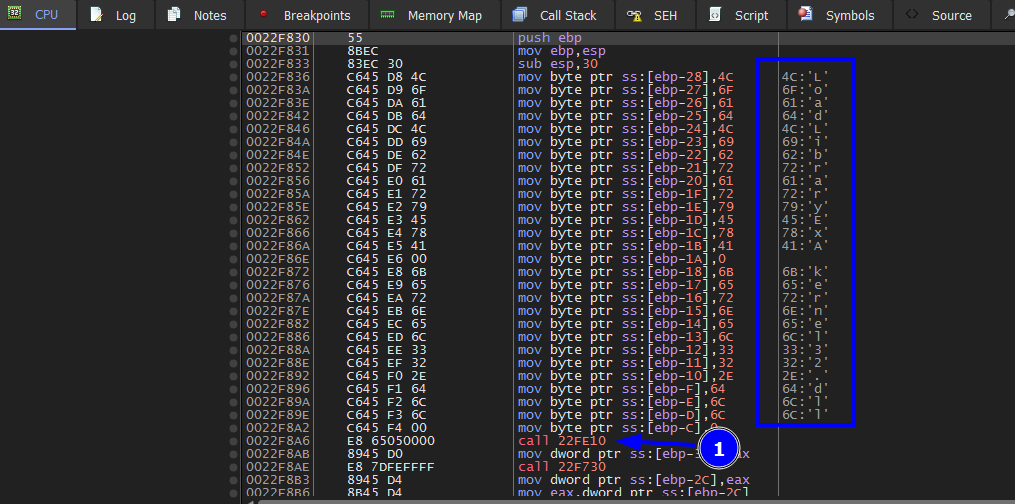
To get out from this function find ret and set a breakpoint then press f9
And these functions do the same as above. So step over them f8.
to see what inside a function without executing it: Double click over a function and press - button to get out.
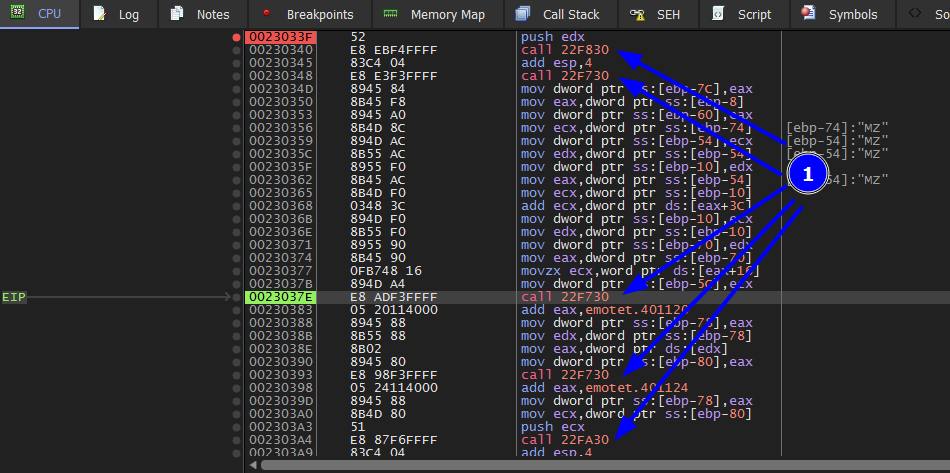
Untill we get to this last function. step into f7.
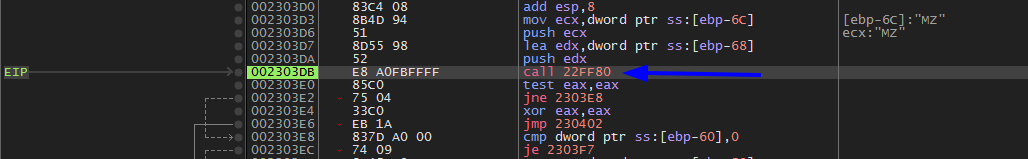
After we get into the function we need to analyze it carefully

As we can see call edx is calling VirtualAlloc:
push 40 RWX which is our indicator to know that this call could be VirtuallAlloc
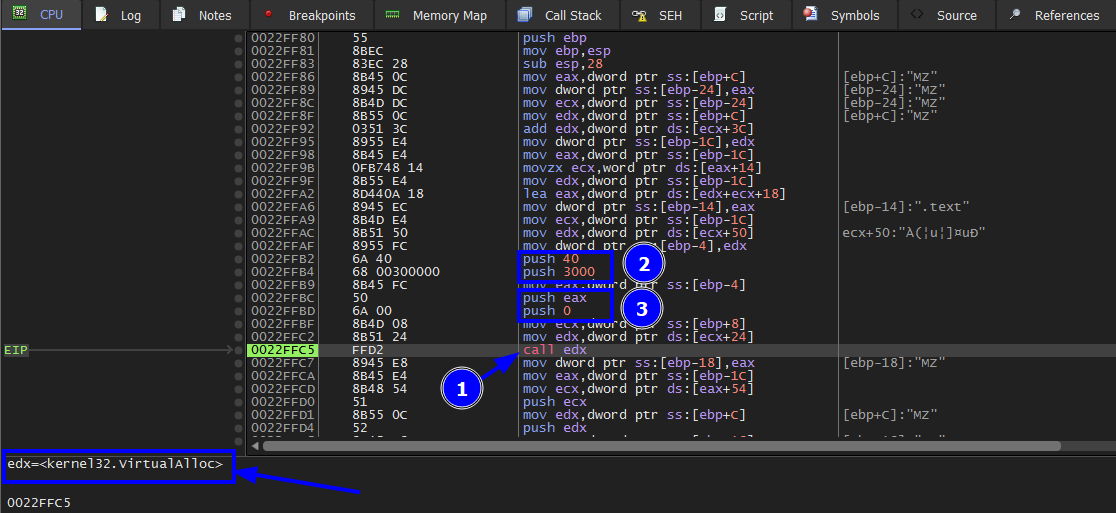
One step over f8 and we will get the adress of newly memory allocated in eax
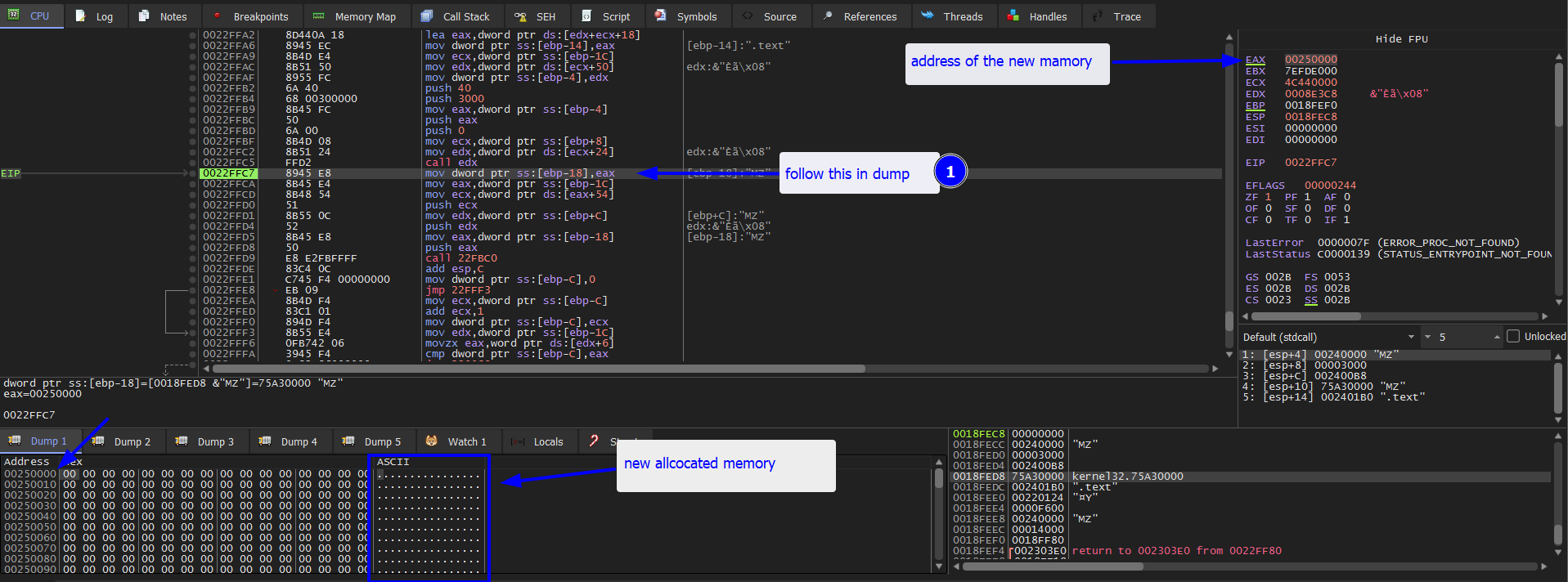
Then keep stepping over and get to this function call 22FBC0 and then one more step over. As we see in the dump section, the function writes over the newly memory allocate with the exe file.
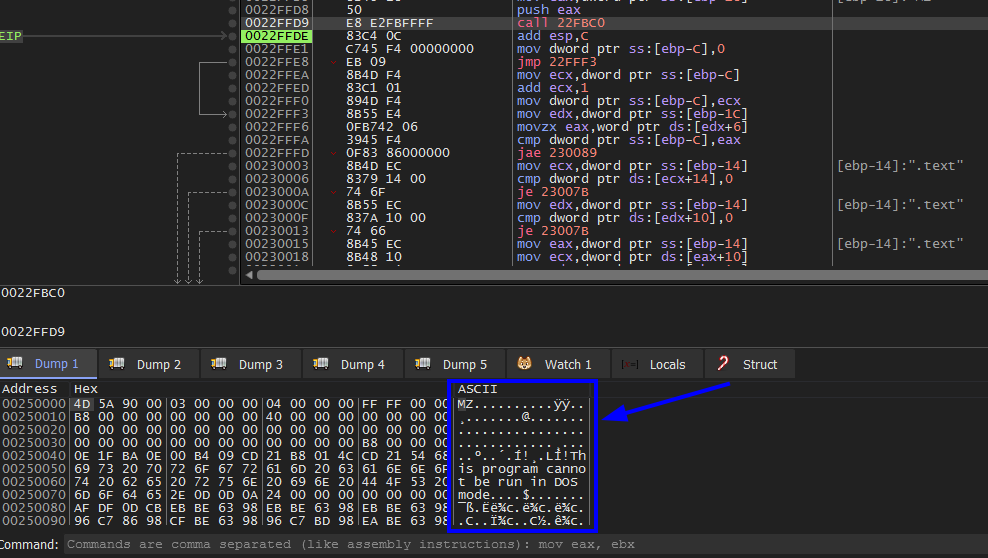
When keep stepping we see that it’s copying files to the exe file
.text
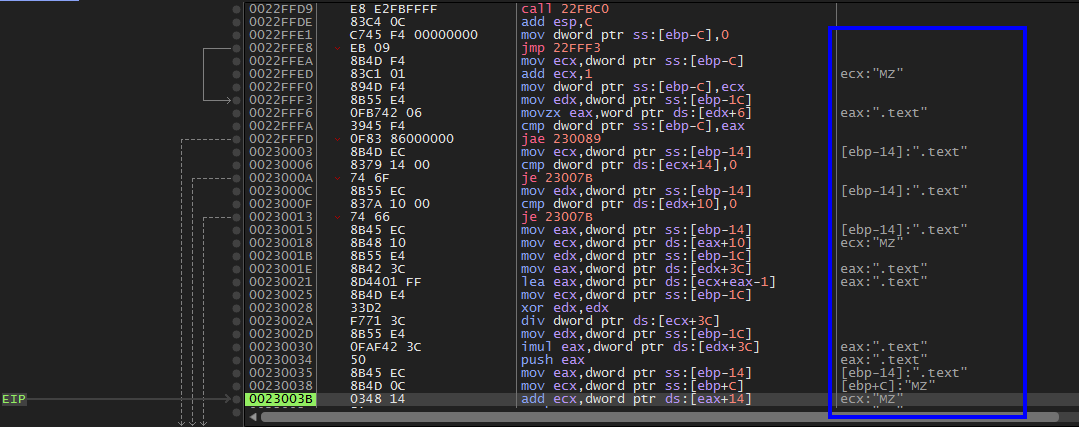
then .rdata then .data then .reloc
Untill we get to the last ret 8 as shown.
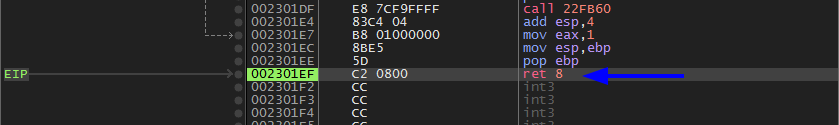
Stay awake our file is almost finished. After the second ret.
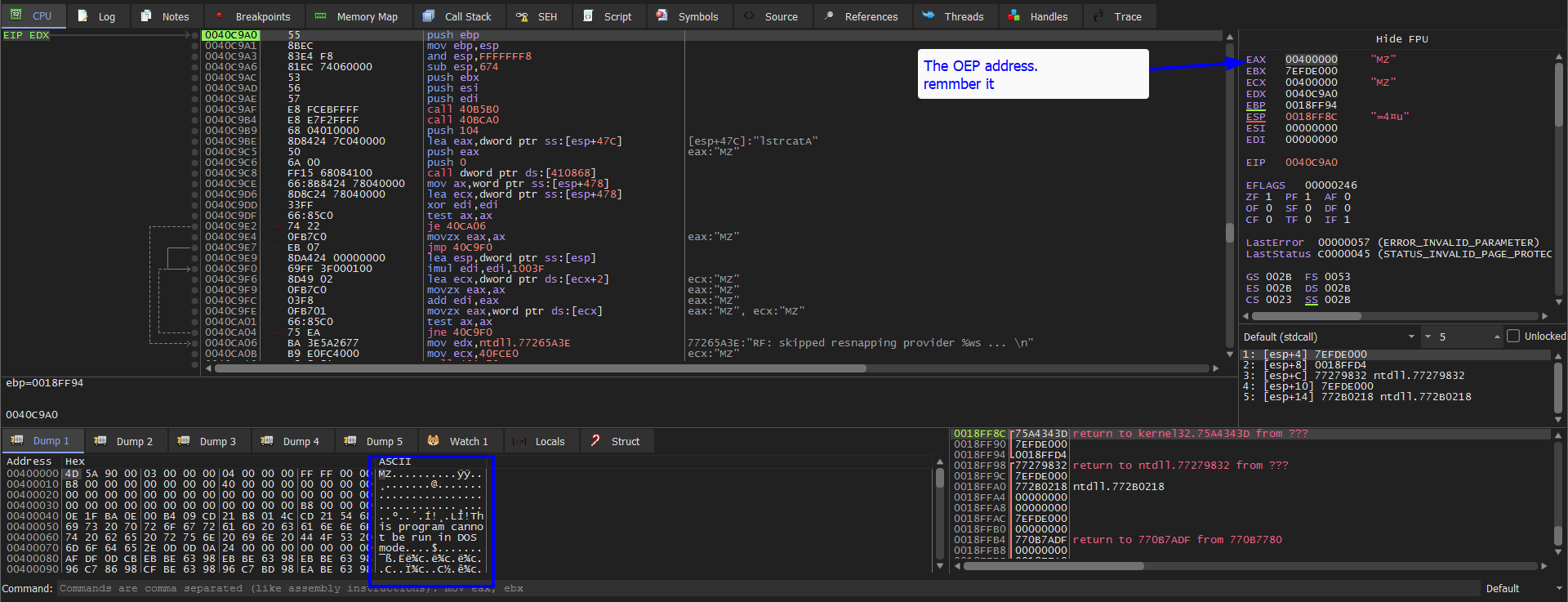
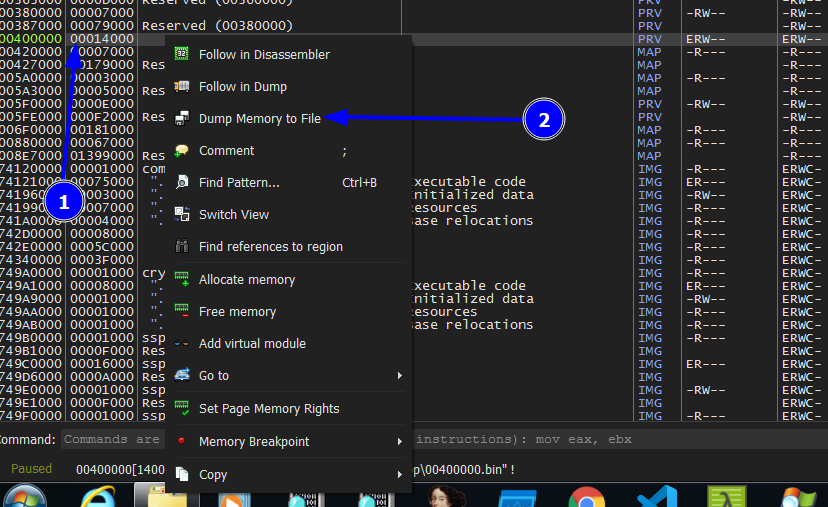
Now we can dump the unpacked exe. right click over eax and press Follow in Mwmory map
Sorry for this Mistake in the next figure. It’s Follow in Mwmory map
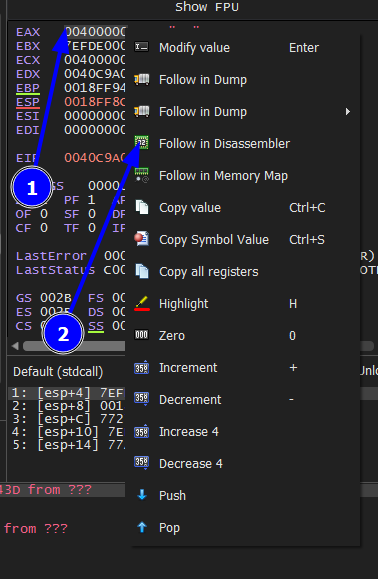
Then right click and then press Dump memory to File
Now if we tried to open it in IDA. We will notice that’s can’t be analyzed
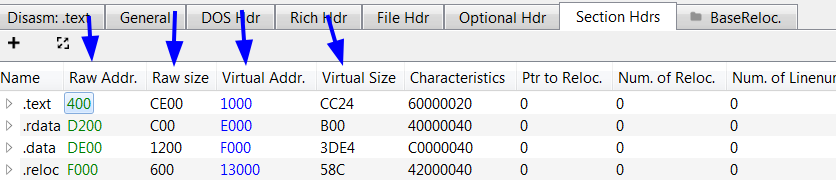
So we need to repair section headers using PE bear tool.
Before
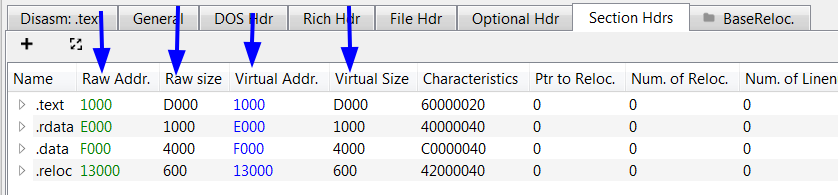
After editing
Then change the image base: if it’s different value of the OEP.
Unmap the unpacked file
How we edit the section headers? ordered steps.
first: copy Virtuall address values into Raw address values.
second: Raw size
Raw size of .test = Raw adress of .rdata - Raw adress of .text
E000 - 1000 = D000
Raw size of .rdata = Raw adress of .data - Raw adress of .rdata
F000 - E000 = 1000
Raw size of .data = Raw adress of .reloc - Raw adress of .data
13000 - F000 = 4000
Raw size of .reloc = still the same
third:
copy Raw size values into Virtual size values.
After changing save the file. This is our unpacked malware
See you in the next article. inshAllah
Article quote
على الضفةِ الأخرى لن نخشى الغرق
Refernces
1- https://www.mcafee.com/blogs/enterprise/malware-packers-use-tricks-avoid-analysis-detection/
3- https://www.0xbyte.com/unpacking-mzp-ransomware-manually/
5- https://msdn.microsoft.com/en-us/library/windows/desktop/aa366887(v=vs.85).aspx
