Unpacking Hancitor malware
As-salamu Alaykum
Introduction
Hancitor is an information stealer and malware downloader used by a threat actor designated as MAN1, Moskalvzapoe or TA511. In a threat brief from 2018, we noted Hancitor was relatively unsophisticated, but it would remain a threat for years to come. Approximately three years later, Hancitor remains a threat and has evolved to use tools like Cobalt Strike. In recent months, this actor began using a network ping tool to help enumerate the Active Directory (AD) environment of infected hosts. This blog illustrates how the threat actor behind Hancitor uses the network ping tool, so security professionals can better identify and block its use. 1
MD5: FF9D0327538AB33468A8AD2142EFF416
Packed indicators
If we open it in DiE or pestudio we will notice that it’s Not packed.
Another way to detect packing is to open it in IDA and if you see less number of functions then It’s packed.
Unpacking process
How unpacking works? well, packing process depands on the packer. So each packer has different unpacking routine.
So in this sample we will begin by setting two breakpoints in VirtualAlloc and VirtualProtect. Then run f9 to hit the first breakpoint and then run again to hit the 2nd one which is VirtualAlloc. Then step over f8to the call of virtualalloc. Then dump EAX.
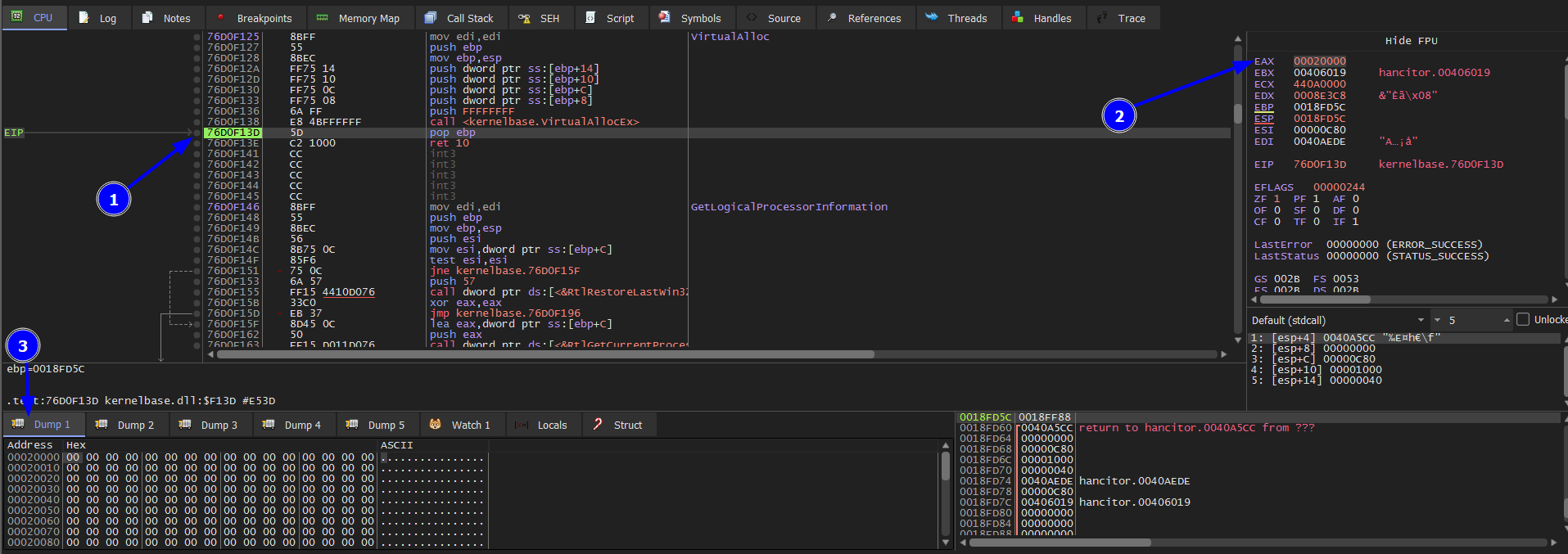
Then run again to get to virtualalloc to the 2nd time and see what dump has.
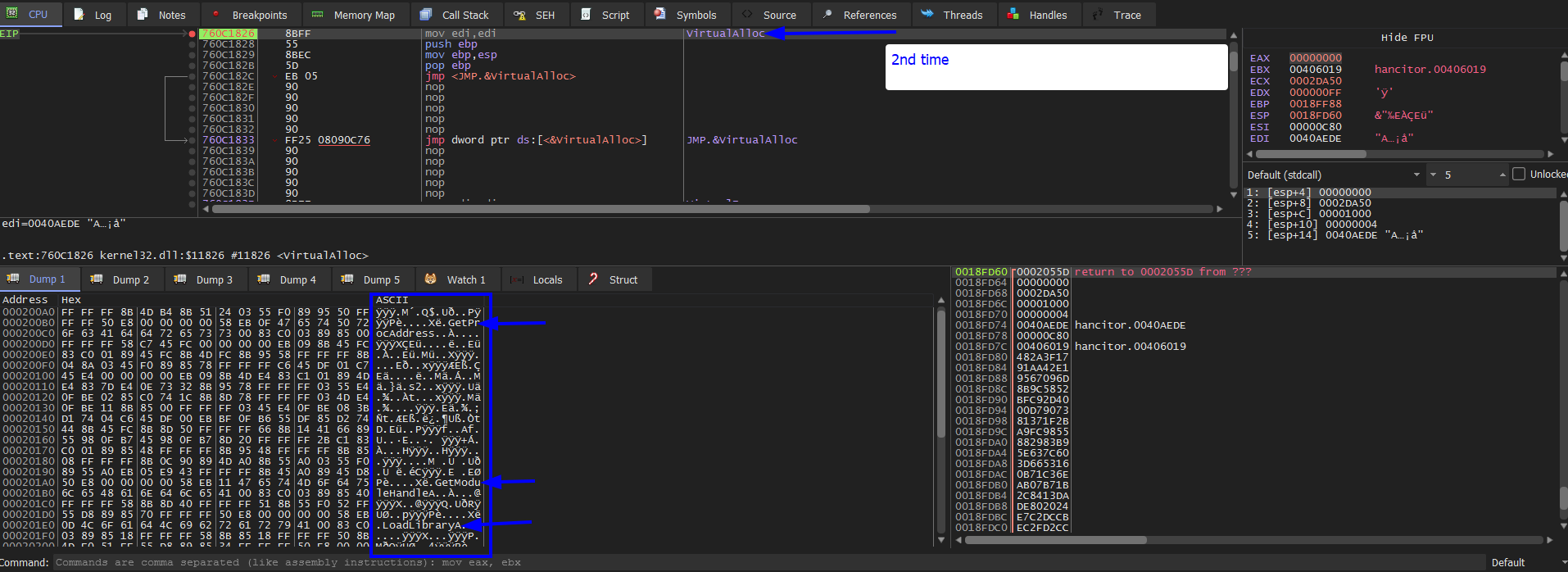
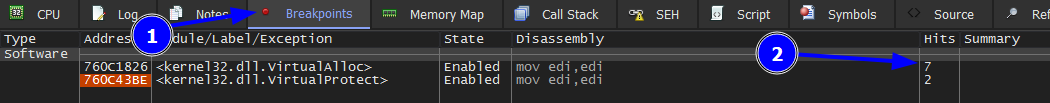
We keep pressing run to hit the breakpoint ofVirtualAlloc 7 times. After that we we hit run again.
We will see our unpacked exe in the dump. Then we Follow in Memory map and save to file. And Image base is 230000.
Unmap the unpacked file
To get improts of the unpacked file. We need to repair the section headers see my article Here. After unmapping you can see Imports and libraries.
Article quote
وماذا يهم إذا لم تكن الحياة على ما يُرام؟
REF
1- https://unit42.paloaltonetworks.com/hancitor-infections-cobalt-strike/
2- VirtualAlloc
